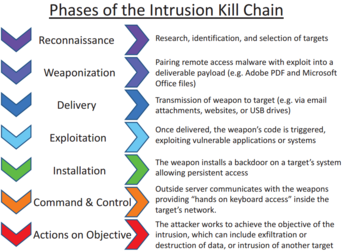
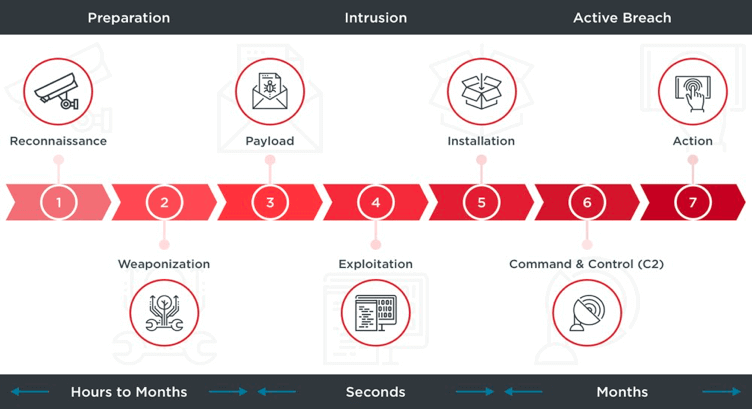
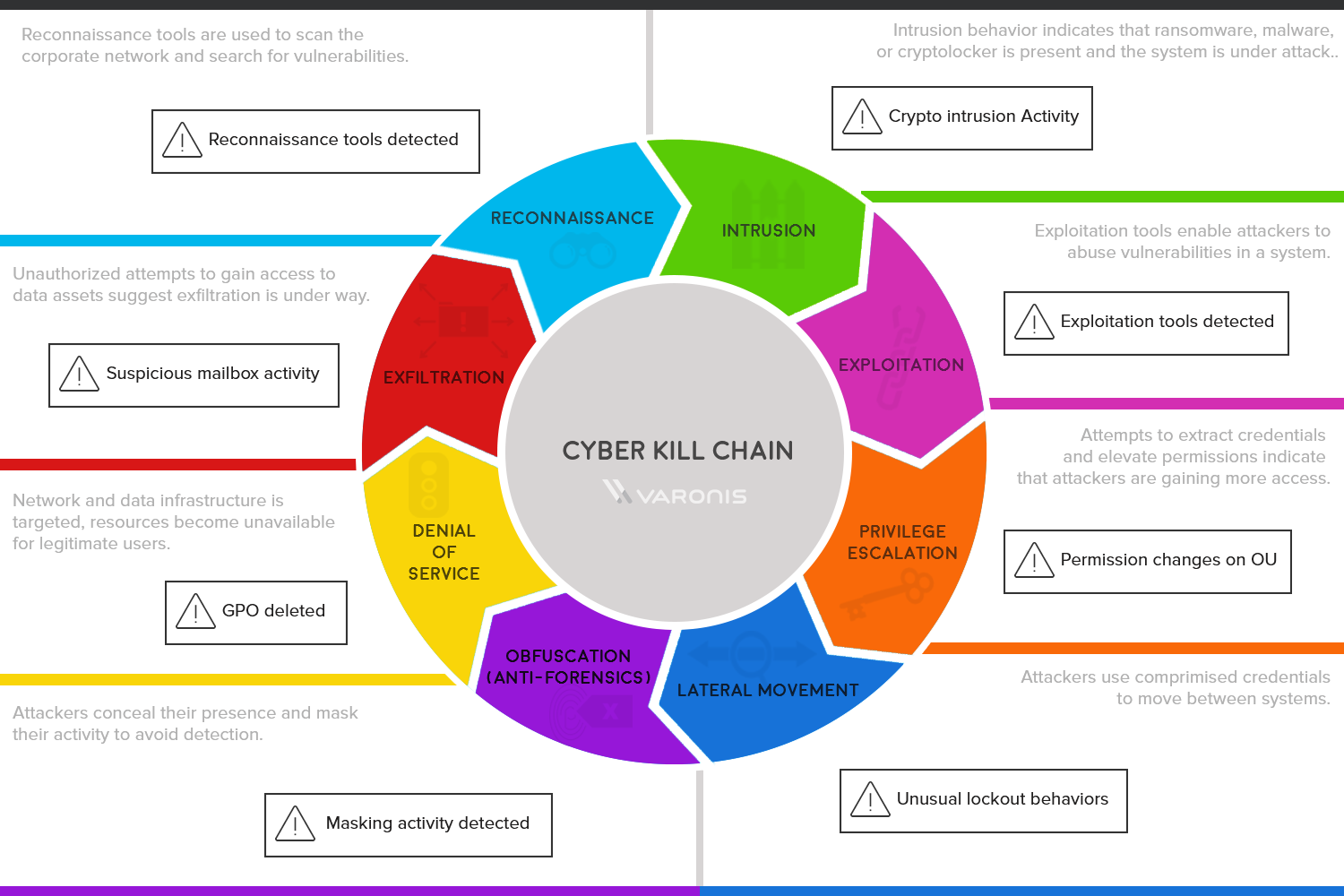
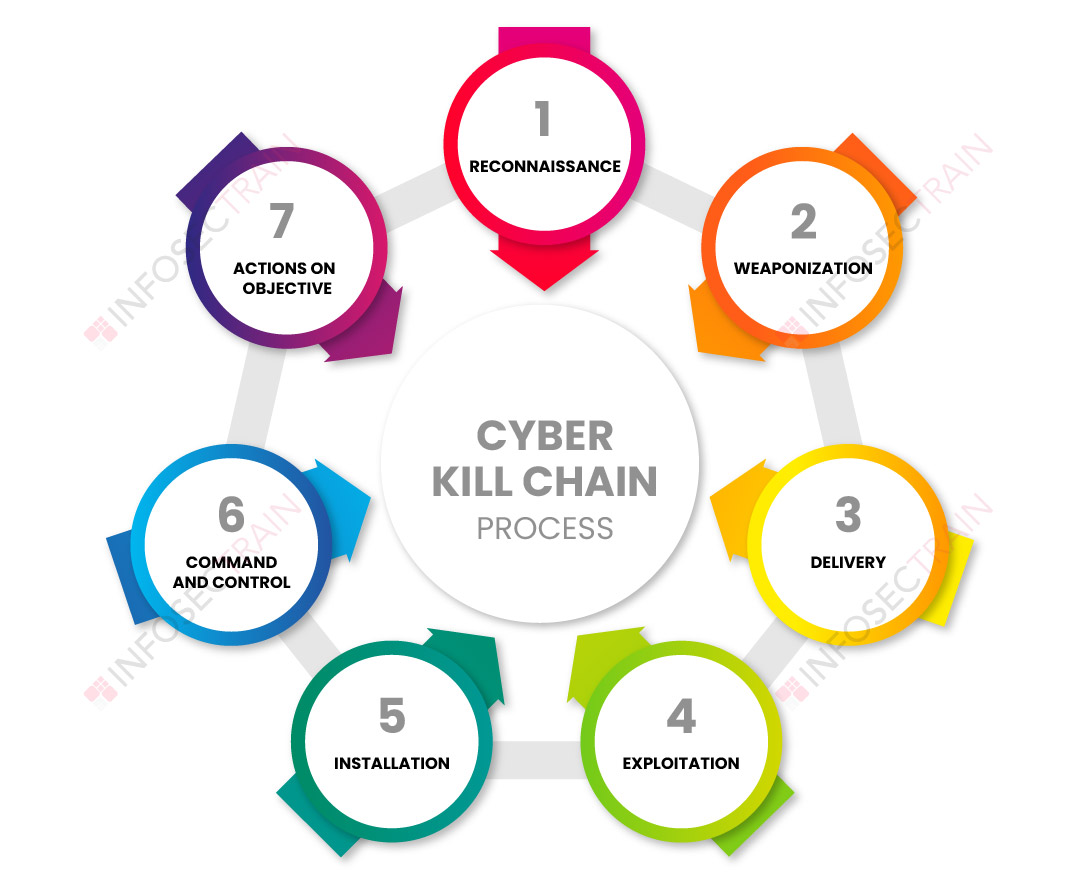
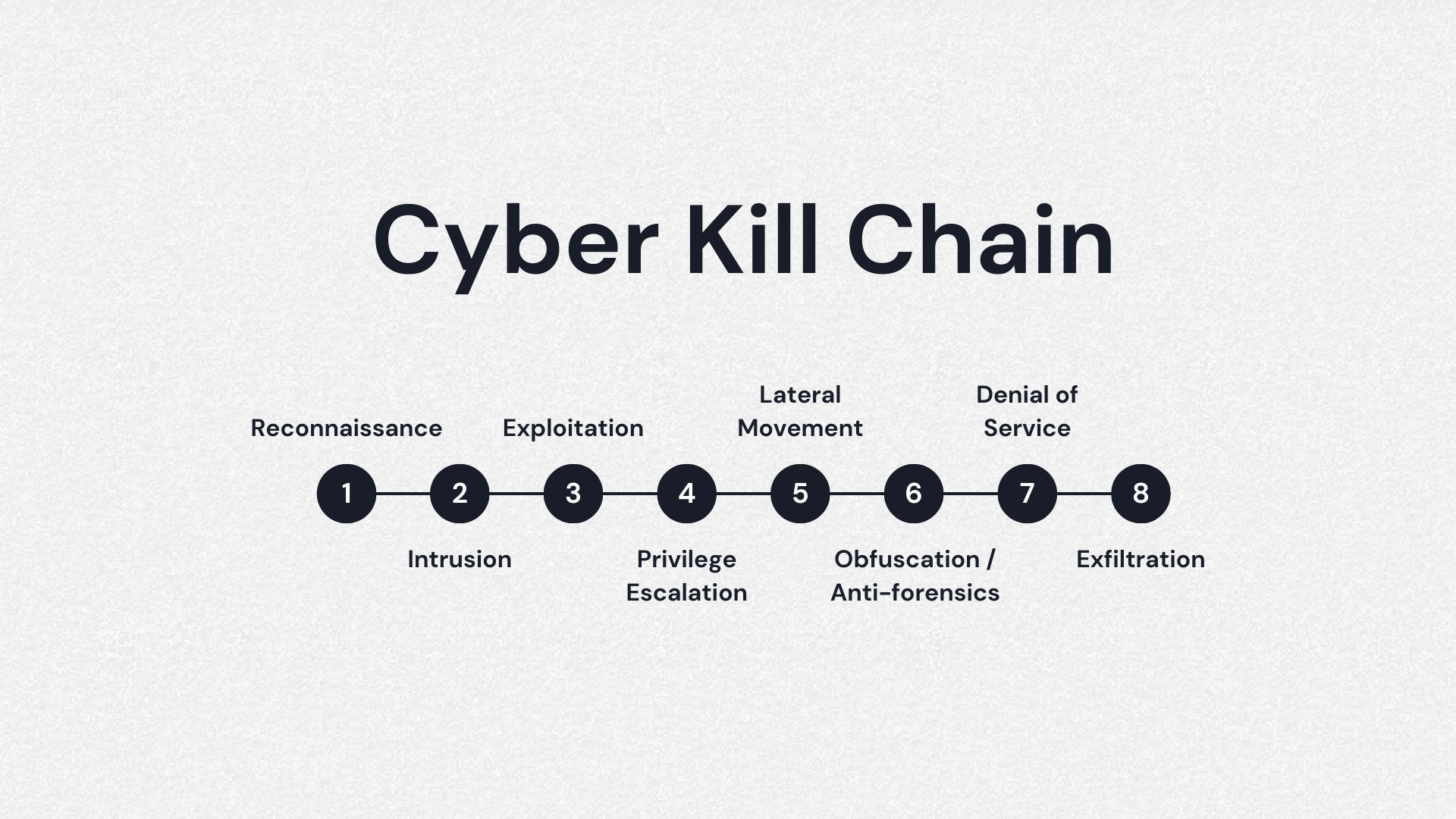
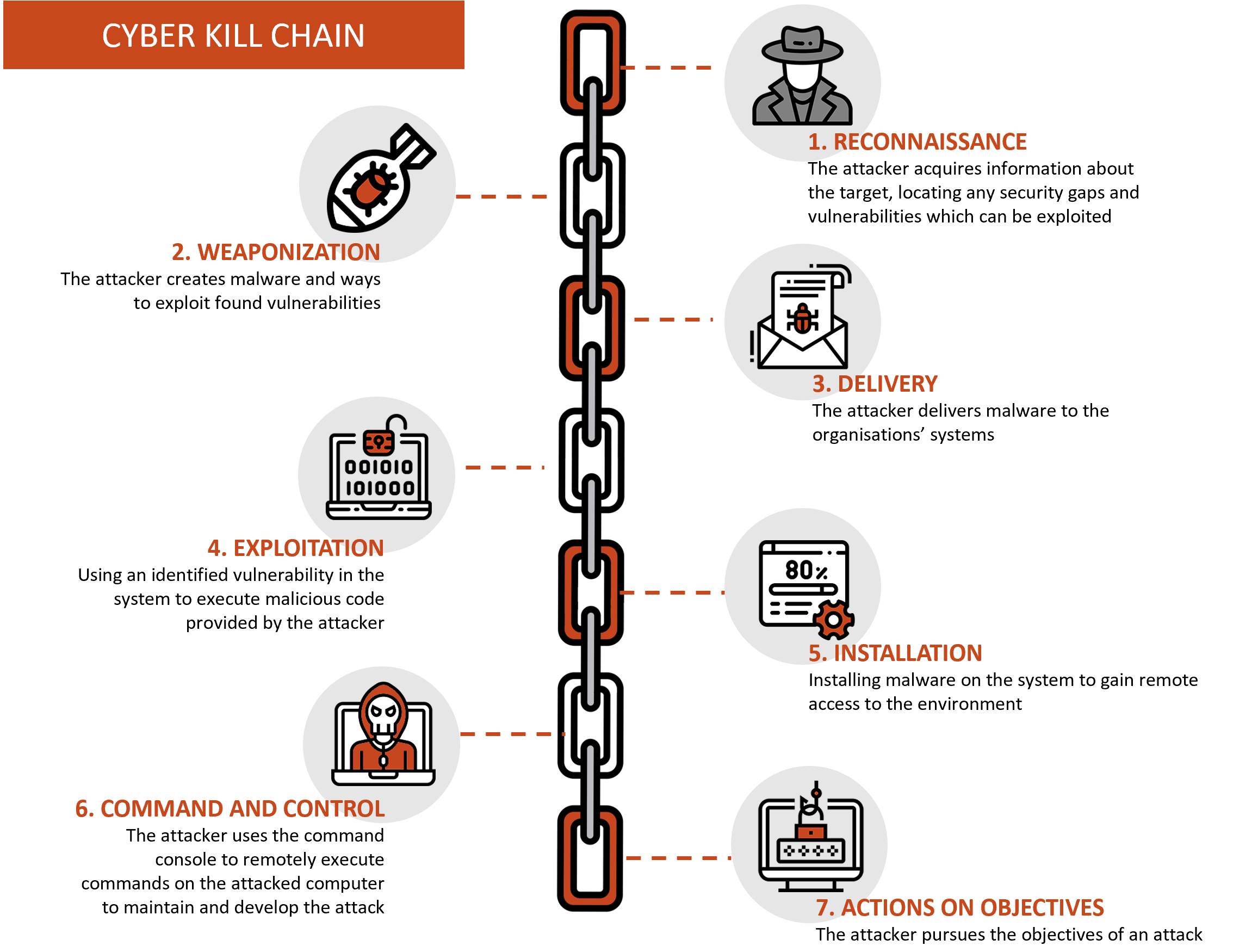
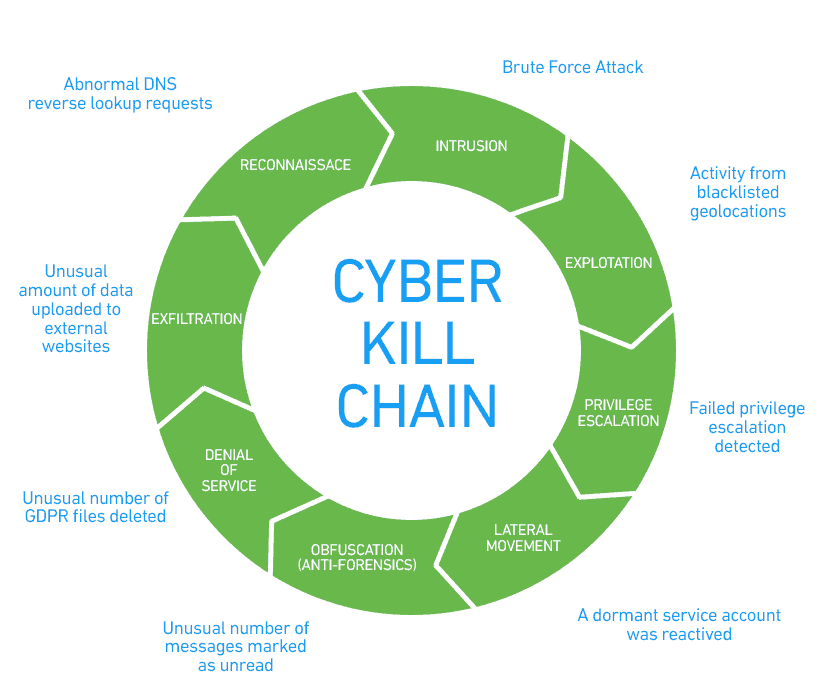
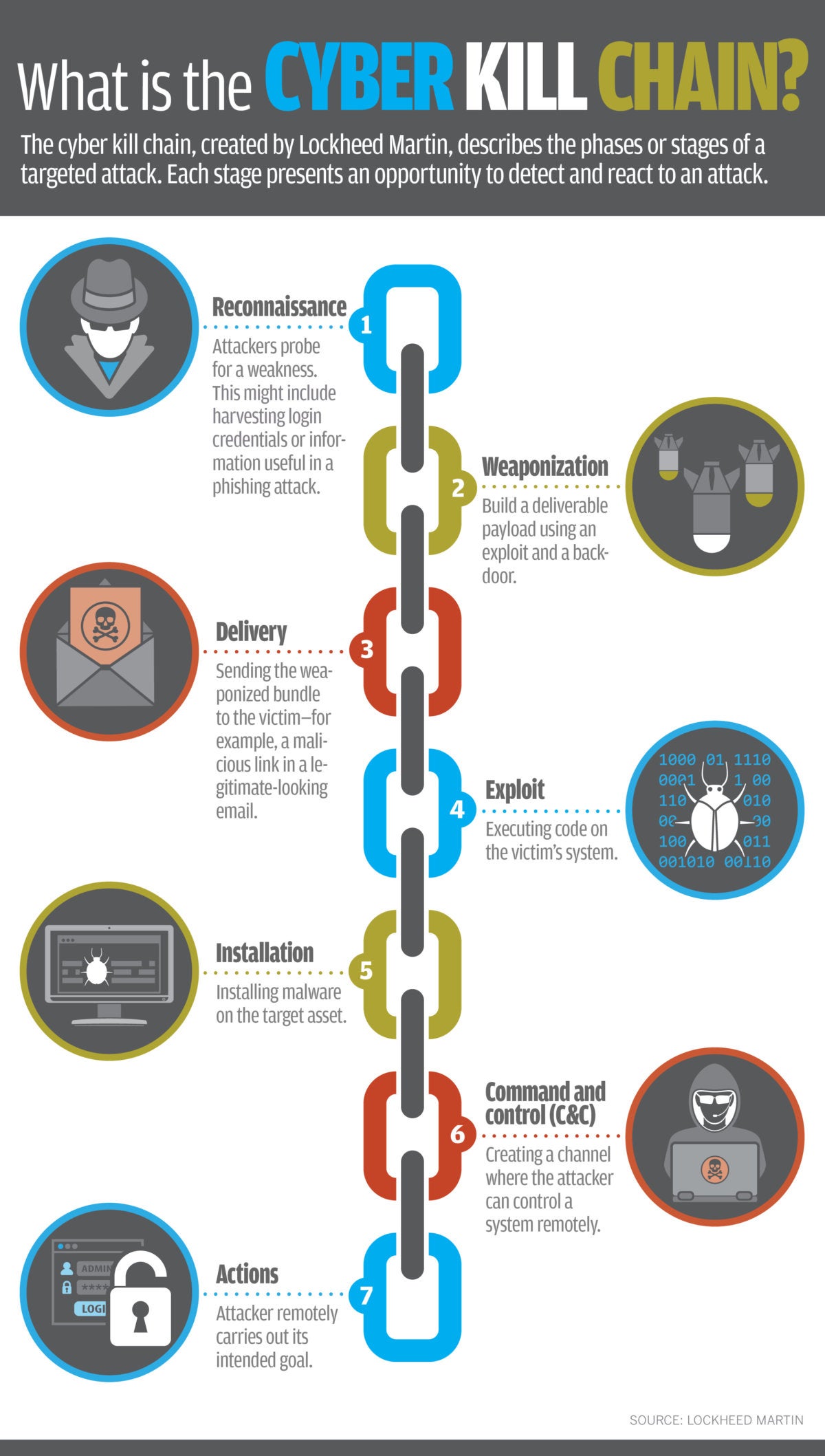
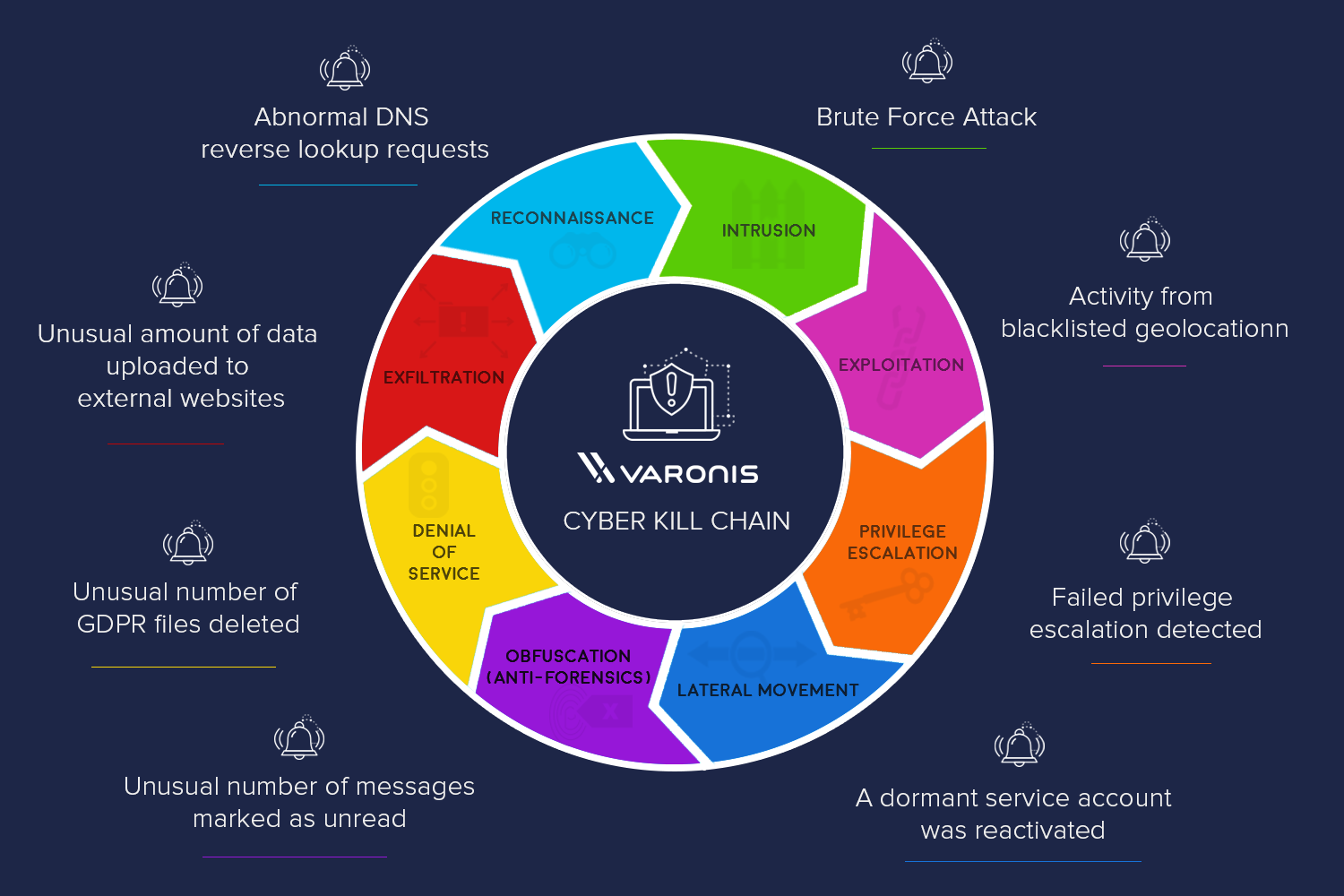
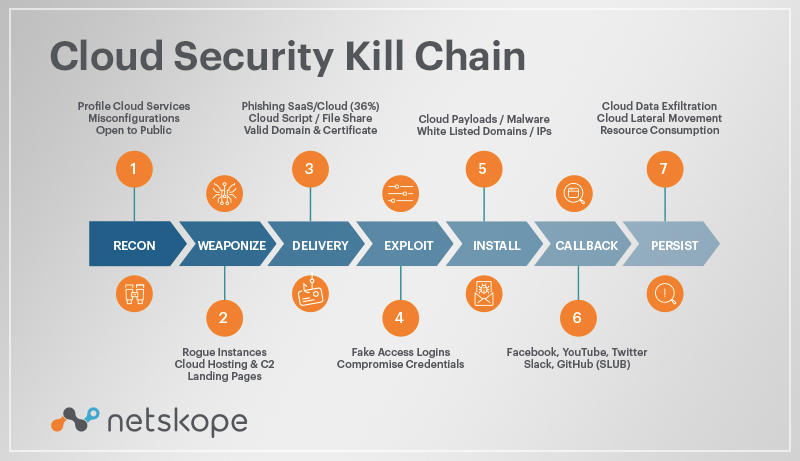
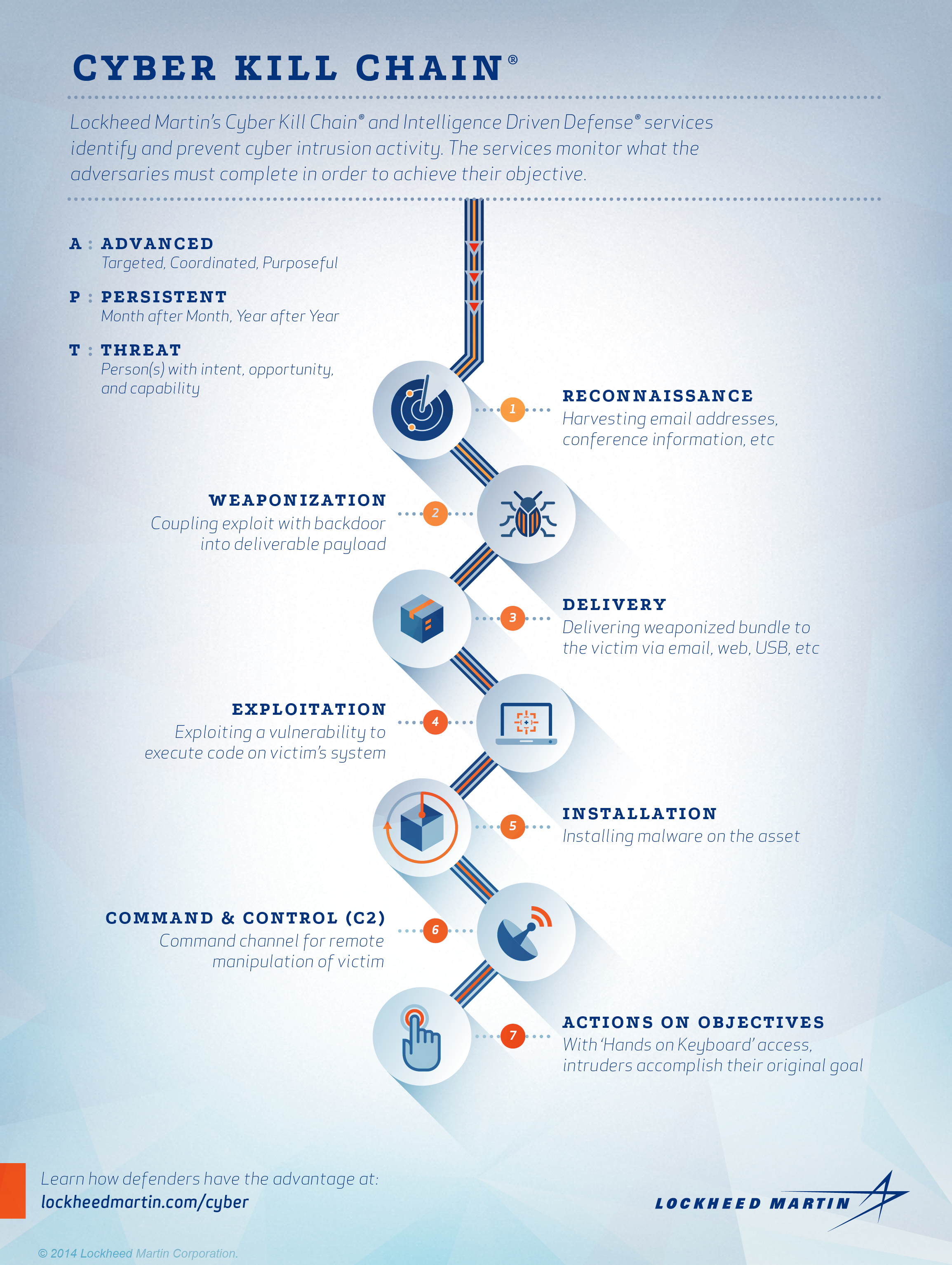
🛡️ Décortiquer la méthodologie de la Cyber Kill Chain : Comprendre et contrer les attaques informatiques étape
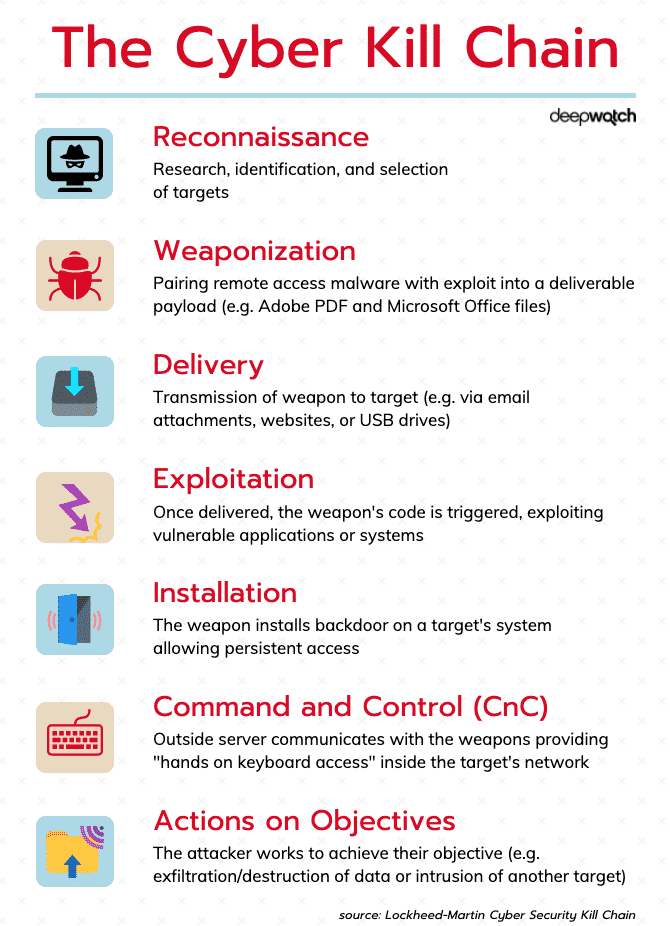
![Lockheed Martin Cyber Kill Chain (CKC) [22] seven steps. The part that... | Download Scientific Diagram Lockheed Martin Cyber Kill Chain (CKC) [22] seven steps. The part that... | Download Scientific Diagram](https://www.researchgate.net/publication/335024682/figure/fig1/AS:789313017098241@1565198296990/Lockheed-Martin-Cyber-Kill-Chain-CKC-22-seven-steps-The-part-that-is-specified-with.png)
Lockheed Martin Cyber Kill Chain (CKC) [22] seven steps. The part that... | Download Scientific Diagram
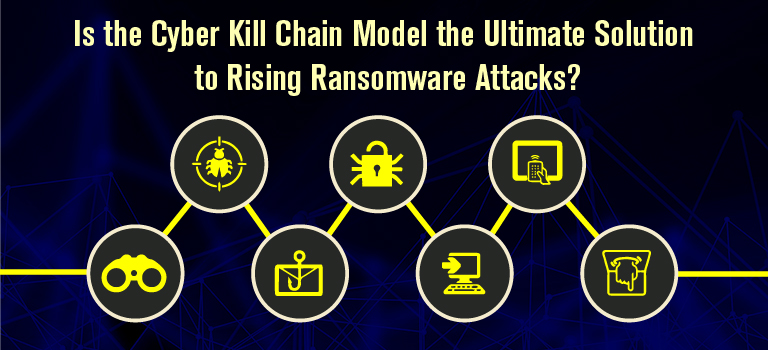
Is the Cyber Kill Chain Model the Ultimate Solution to Rising Ransomware Attacks? - United States Cybersecurity Magazine
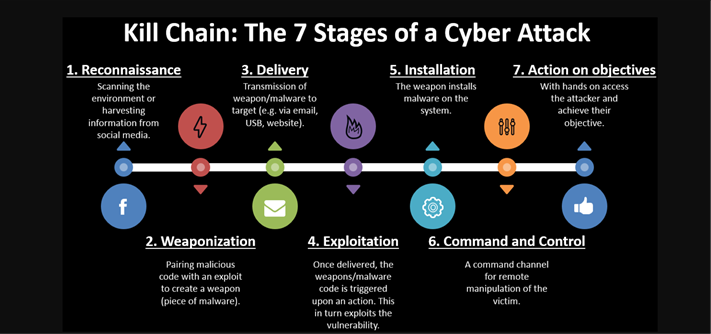









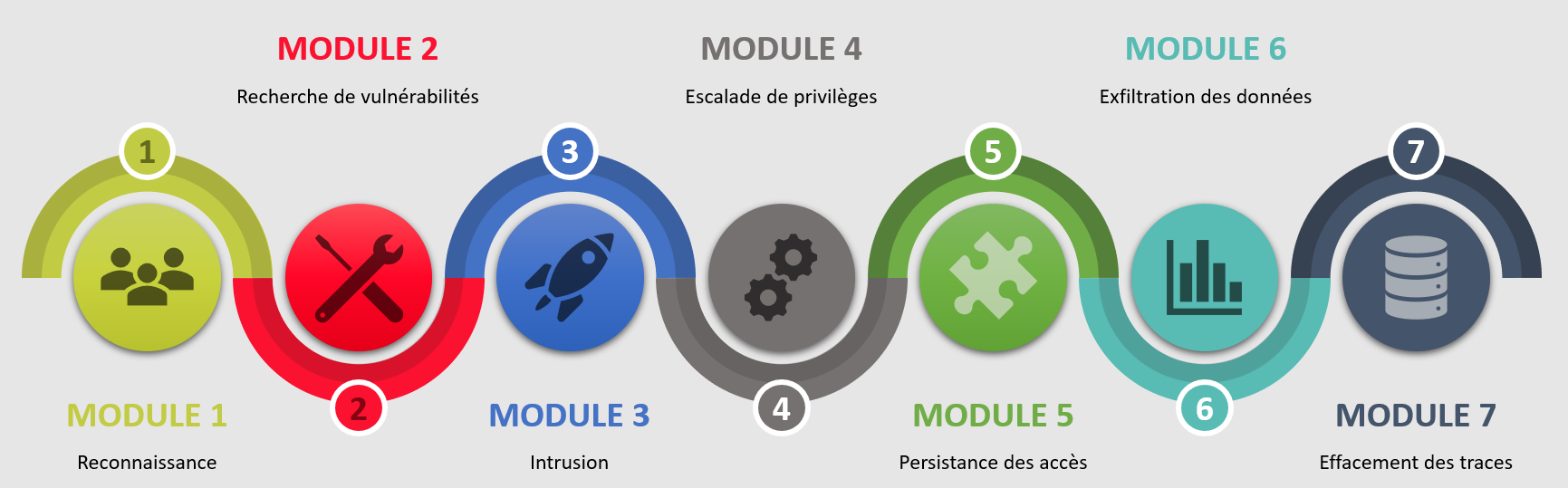
![Infographie] La Cyber Kill Chain en 7 étapes - MANIKA Infographie] La Cyber Kill Chain en 7 étapes - MANIKA](https://www.manika-consulting.com/wp-content/uploads/2021/01/Infographie-Cyber-Kill-Chain.png)